Cryptojacking, or malicious cryptocurrency mining, is a type of cybercrime where hackers use victims’ devices (computers, smartphones, tablets, or servers) to mine cryptocurrencies without their knowledge.
Simply put, cryptojacking occurs when a hacker infects your device unnoticed and uses it to mine cryptocurrency for their own benefit.
How Does Cryptojacking Work?
To keep blockchain networks running, significant resources are necessary:
1) Computational power. For example, modern miners can cost anywhere from $4,000 to $6,000.
2) Energy to fuel these operations
Bitcoin stands as the most prominent blockchain network. It consumes over 73 TWh of energy annually (as of 2024) to perform computations and add new blocks to its chain.
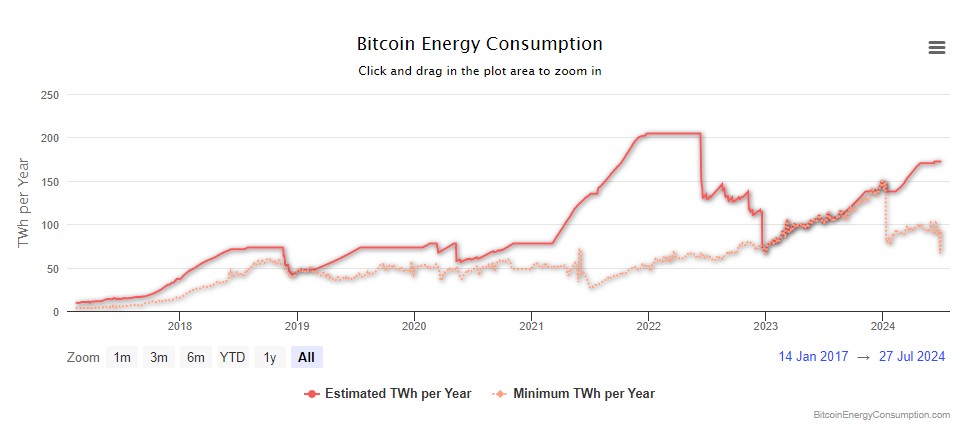
Being a miner comes with substantial costs. It is a different story when these burdens are shifted onto unsuspecting individuals.
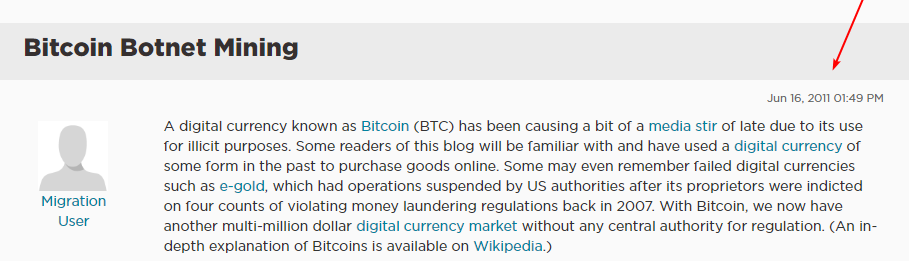
The concept emerged almost immediately with Bitcoin’s inception. As early as 2011, discussions on forums explored cryptocurrency mining within botnets.
As cryptocurrencies gained popularity, interest in cryptojacking also grew.
Scale is crucial for hackers in this regard. Installing malware on an average computer with an integrated graphics card will not yield profits, but infecting a large number of devices can compensate for the efforts through acquired cryptocurrency.
Examples of Cryptojacking
- In 2018, hackers installed malicious code on the Los Angeles Times pages.
- In February 2018, it was discovered that Tesla Inc. had fallen victim to cryptojacking.
- In 2019, programs utilizing cryptojacking were found in the Microsoft Store.
Perhaps the most well-known example is the Coin-hive project, which implemented JavaScript code for mining the Monero coin.
The code could be embedded in websites and applications (even by hackers) like an advertisement. Activating the code allowed the website visitor’s processor to be used for mining cryptocurrency while they consumed content, with the site or app owner receiving a percentage of the mined Monero coins.
The choice of Monero for mining was not random. This blockchain uses privacy-enhancing technologies to hide transactions, aiming for anonymity. Interestingly, the real identity of one of Monero’s main creators remains unknown, similar to Bitcoin’s creator, Satoshi Nakamoto.
At its peak, the Coinhive code was found on streaming platforms like Showtime, news websites, and in Starbucks’ Wi-Fi networks. It was also discovered that Coinhive was operating in YouTube ads through Google’s DoubleClick platform and was installed on 200,000 MicroTik routers in Brazil.
In March 2019, the Coinhive project was shut down by law enforcement, but the issue of cryptojacking remains prevalent.
Cryptojacking. Is It Legal?
No.
Cryptojacking is typically an illegal activity involving unauthorized cryptocurrency mining, as discussed earlier.
However, mining cryptocurrency on users’ devices can be consensual and sometimes even beneficial. For example:
- Content monetization. A website (game) visitor may allow cryptocurrency mining on their device, creating a mutual benefit: the user enjoys interesting content, while the creator uses the computing power for mining. Once the user stops engaging with the content, mining stops, encouraging creators to develop attractive content to retain users.
- Installing mining software. Services like NiceHash allow users to install software for legal cryptocurrency mining.

However, as soon as the user stops voluntarily allowing their device to be used for mining, it becomes cryptojacking.
How Does Cryptojacking Code Infect Devices?
The code that hijacks device resources can be introduced in several ways:
- Web Browsers. Malicious scripts can be embedded into websites. When a user visits such a site, the script runs and uses the device’s resources for hidden cryptocurrency mining.
- Downloads. Users might inadvertently download and install malicious software disguised as legitimate applications or files. This can happen through phishing attacks or downloads from untrustworthy sources.
- Mobile apps. Hackers can create or modify mobile applications that begin mining cryptocurrency once installed on a device. Such apps can even appear in official stores, although this is less common due to efforts to remove them.
Cryptojacking Threats:
- Device wear and tear. Continuous high load and overheating can reduce a device’s lifespan.
- Higher energy bills. Increased energy consumption leads to higher electricity costs.
- Performance issues. Infected devices operate more slowly.
- Data security risks. Malware can give hackers access to your personal data.
Signs Your Device Is Infected:
- Noticeable performance drop;
- Device overheating;
- Freezing due to lack of processing power.
- Unexpectedly high electricity bills or rapid phone battery drain.
How to Avoid Becoming a Victim
To protect yourself from cryptojacking:
- Use antivirus software. Regularly update your operating system and applications to patch vulnerabilities.
- Consider blocking scripts and ads in your browser. Install browser extensions like NoScript, MinerBlock, or ad blockers to prevent malicious scripts and ads often used for cryptojacking.
- Be careful with downloads and apps. Only download software and files from official and trusted sources. Check the permissions requested by mobile apps, read user reviews, and avoid installing unnecessary apps.
Conclusions
Cryptojacking is enabled by three main factors:
- The ingenuity and determination of hackers to exploit other people’s computing resources.
- The rising value of cryptocurrencies, which makes mining potentially profitable.
- Users’ carelessness and lack of attention.
It is believed that the peak of cryptojacking was in 2018, but that does not mean someone could not be secretly using your computer to mine cryptocurrencies today.
Download ATAS for free. This program does not protect against cryptojacking but enables you to legally earn cryptocurrency from trading on reliable exchanges.
User data needed for ATAS to work is stored locally on local computers in encrypted form. User keys are not stored on company servers, and trading is conducted directly from your computer with a connection to the exchange’s servers.
During the trial period, you will be able to experiment with various strategies using access to platform tools such as:
- DOM Levels, market profiles, and other indicators;
- ATAS Smart DOM, ATAS Smart Tape;
- a Market Replay trader simulator;
- custom time frames, flexible settings, and much more.
Once you install the platform, you will automatically get the free START plan, which includes cryptocurrency trading and basic features. You can use this plan for as long as you like before deciding to upgrade to a more advanced plan for additional ATAS tools. You can also activate the Free Trial at any time, giving you 14 days of full access to all the platform’s features. This trial allows you to explore the benefits of higher-tier plans and make a well-informed decision about purchasing.
Do not miss the next article on our blog. Subscribe to our Youtube channel, follow us on Facebook, Instagram, Telegram or X, where we publish the latest ATAS news.
Information in this article cannot be perceived as a call for investing or buying/selling of any asset on the exchange. All situations, discussed in the article, are provided with the purpose of getting acquainted with the functionality and advantages of the ATAS platform.